Understanding AWS Security Groups and Bootstrap Scripts: Enhancing Cloud Security and Automation.
In the realm of AWS, achieving a balance between robust security and streamlined automation is essential for efficient cloud management. AWS Security Groups and Bootstrap Scripts play pivotal roles in this Endeavor. In this article, we’ll delve into these two AWS components and provide a hands-on demo to illustrate how to leverage them effectively.
AWS Security Groups:

What are AWS Security Groups?
AWS Security Groups are a fundamental element of AWS’s network security model. They act as virtual firewalls for your instances to control inbound and outbound traffic. Security Groups are associated with AWS resources like EC2 instances and RDS databases and allow you to define inbound and outbound rules that control traffic to and from these resources.
Key Features of AWS Security Groups:
Stateful: Security Groups are stateful, meaning if you allow inbound traffic from a specific IP address, the corresponding outbound traffic is automatically allowed. This simplifies rule management.
Default Deny: By default, Security Groups deny all inbound traffic. You must explicitly define rules to allow traffic.
Dynamic Updates: You can modify Security Group rules anytime to adapt to changing security requirements.
Use Cases:
Web Servers: Security Groups are used to permit HTTP (port 80) and HTTPS (port 443) traffic for web servers while denying other unwanted traffic.
Database Servers: For database servers, Security Groups can be configured to only allow connections from known application servers while blocking access from the public internet.
Bastion Hosts: In a secure architecture, a bastion host’s Security Group can be set up to allow SSH (port 22) access only for specific administrators.
Demo: Creation of security group to open port 22 for SSH, port 80 for HTTP, and port 443 for HHTPS.
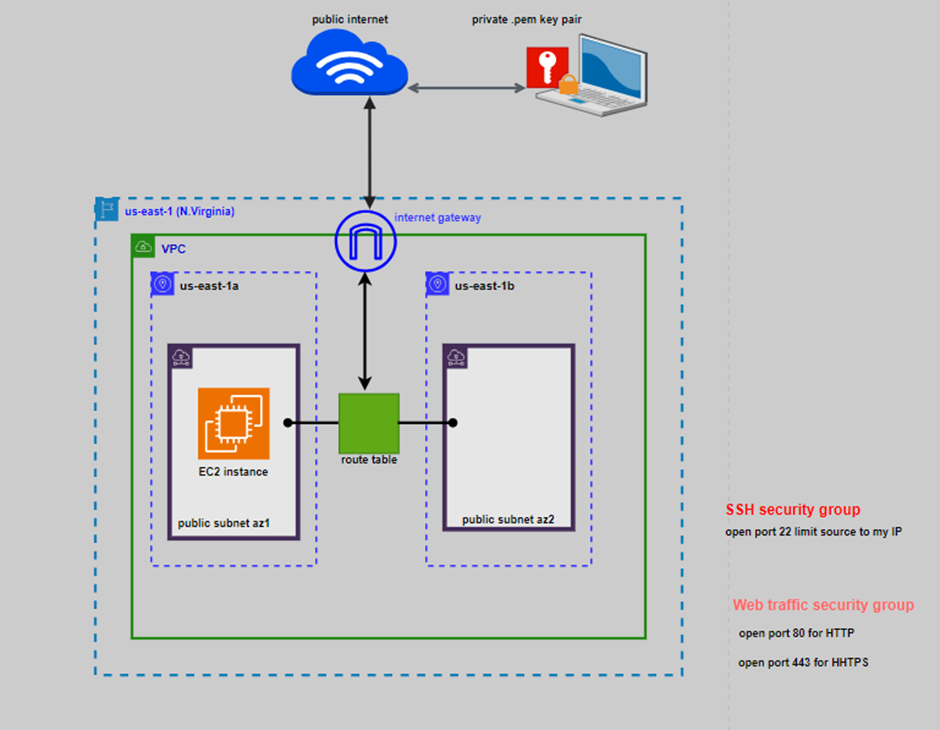
To create security group, click on this link and follow our previous demo on the security group.
Bootstrap Scripts
What are Bootstrap Scripts?
A bootstrap script, often referred to as user data or initialization script, is a piece of code or script that is executed when an EC2 instance is launched for the first time. This script automates the setup and configuration of the instance, making it ready for use. Bootstrap scripts are highly customizable and allow you to install software, configure settings, and perform various tasks during instance initialization.
Key Features of Bootstrap Scripts:
Automation: Bootstrap scripts automate the instance setup and configuration process, reducing manual intervention and potential errors.
Flexibility: You have full control over the contents and execution of the script, making it adaptable to your specific use case.
Idempotent: Bootstrap scripts can be designed to be idempotent, meaning they can be run multiple times without causing adverse effects.
Use Cases:
Software Installation: You can use bootstrap scripts to install and configure specific software packages on an instance.
Configuration: Configure instance settings, such as setting environment variables or customizing application parameters.
Automated Tasks: Run scripts for backups, log rotation, and other routine maintenance tasks.
Combining Security Groups and Bootstrap Scripts
The synergy between Security Groups and Bootstrap Scripts offers a robust approach to enhancing both security and automation in your AWS environment.
Security Controls: Security Groups ensure that only authorized traffic is allowed to and from your EC2 instances. Bootstrap scripts can automate the process of ensuring that your instances are configured securely from the moment they launch.
Dynamic Updates: In response to changing security needs, Bootstrap Scripts can automatically update instance configurations.
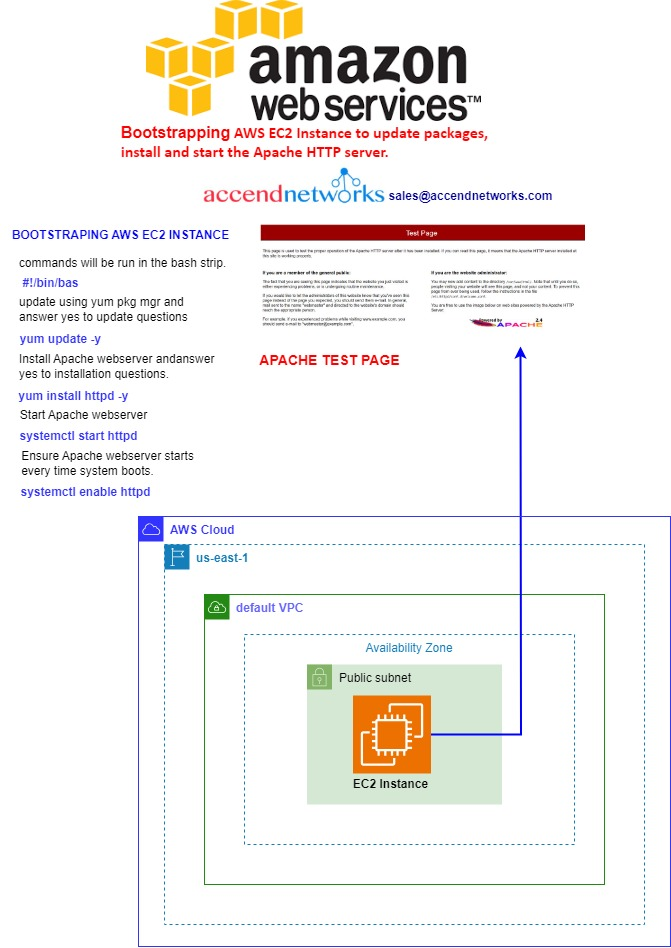
Demo: Bootstrapping AWS EC2 Instance to update packages, install and start Apache HTTP server. (HTTP is on port 80)
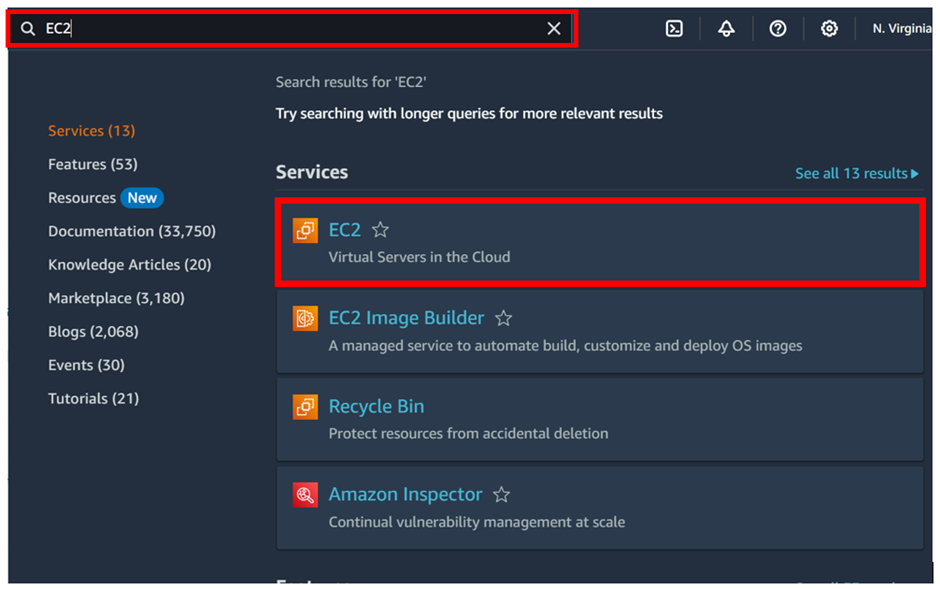
sign in to your AWS Management Console, type EC2 in the search box then select EC2 under services
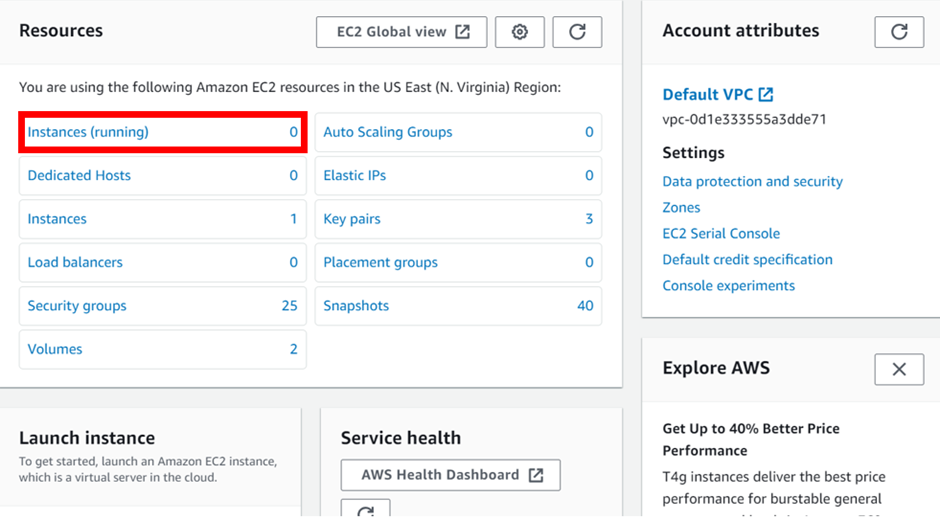
In the EC2 dashboard, select instances then click launch
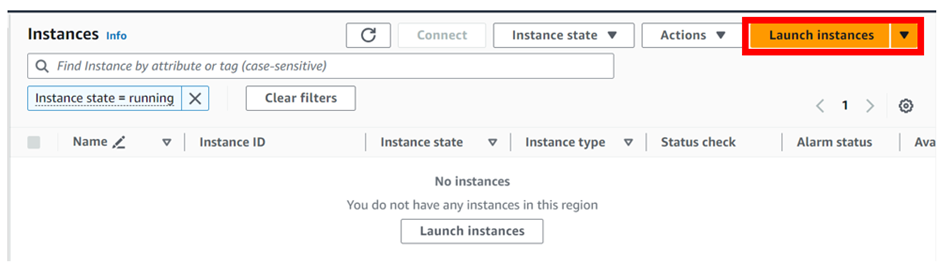
In the launch instance dashboard, under name and tags, give your instance a name. call it bootstrap-demo-server.
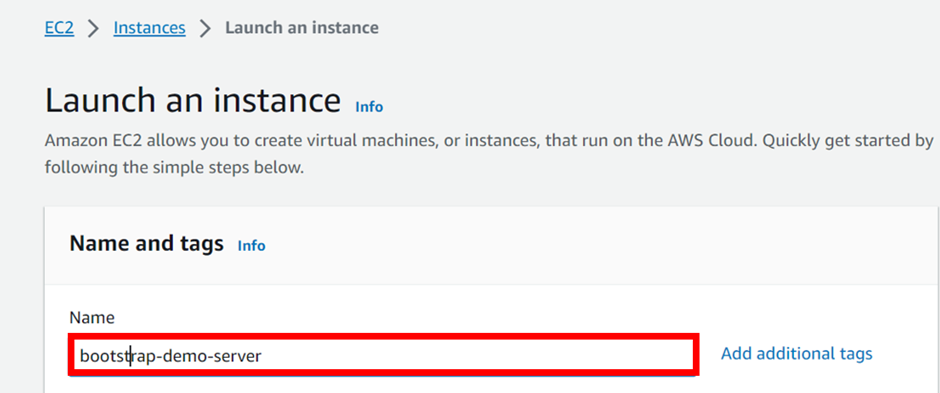
Under application and OS images, select the QuickStart tab then select Amazon Linux. Under Amazon Machine Image (AMI), select the drop-down button and select Amazon Linux 2 AMI. Scroll down.
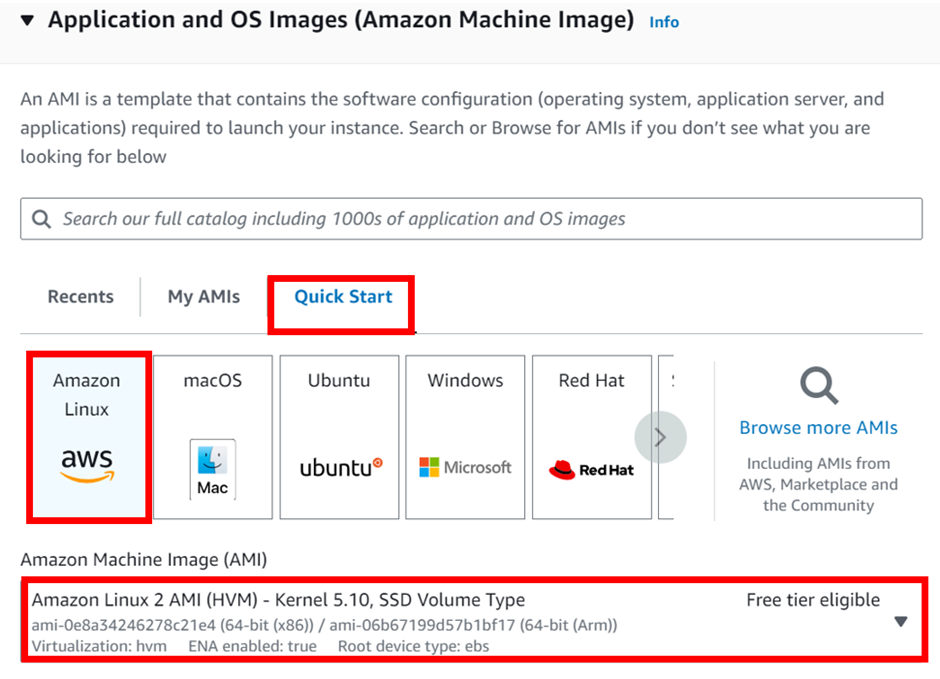
Under instance type make sure it is t2. Micro because it is the free-tier one. Under keypair login select the dropdown and select your key-pair. Scroll down.
We will leave all the other options as default move all the way to the advanced details section, then click the drop-down button to expand it.
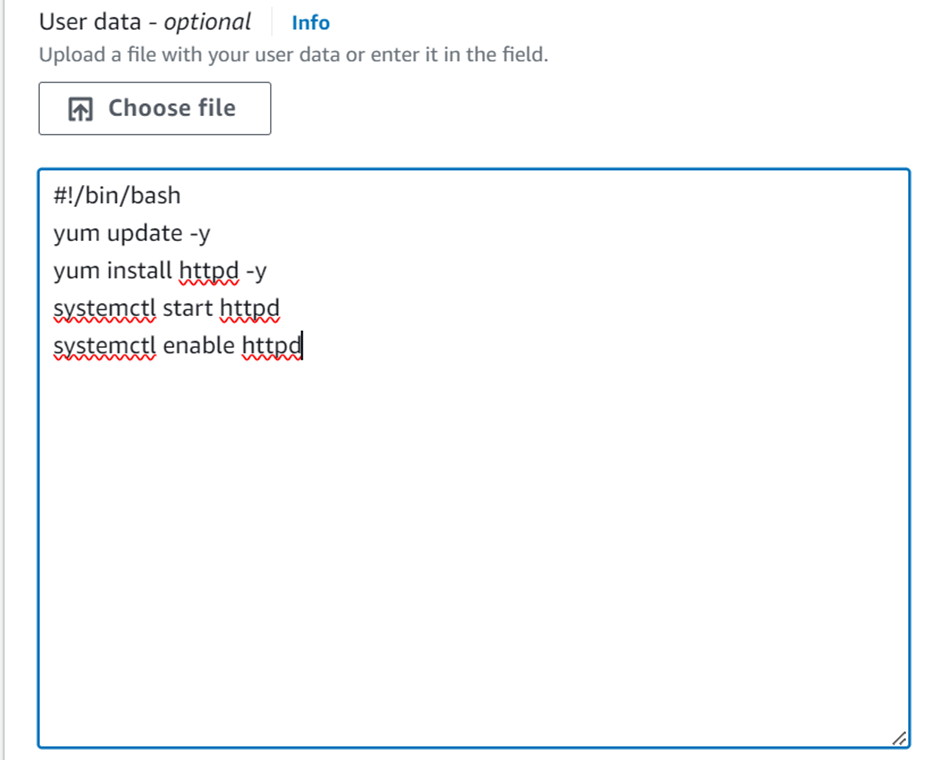
Move all the way down to the instance user data section. Copy and paste this code inside there.
- #!/bin/bash
- yum update -y
- yum install httpd -y
- systemctl start httpd
- systemctl enable httpd
Tip: Once the instance is launched and you may have to go back and modify this User Data section, stop the instance, click Actions-Instance settings-Edit user data.
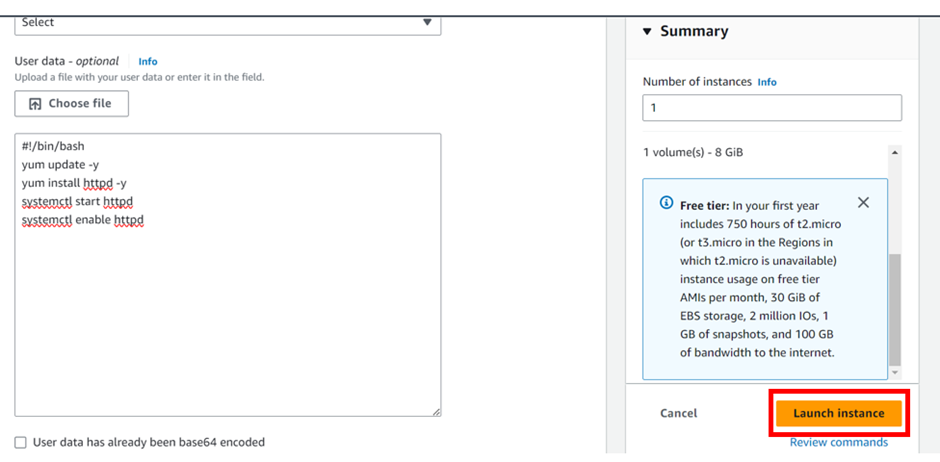
Under instance, summary, review, and click launch instance.

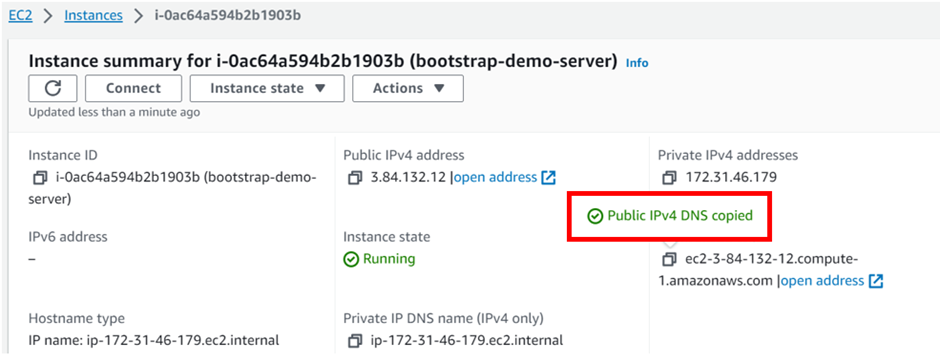
Click on the instance ID then wait for the status check to initialize. Copy the public IPv4 DNS and paste it into your browser.
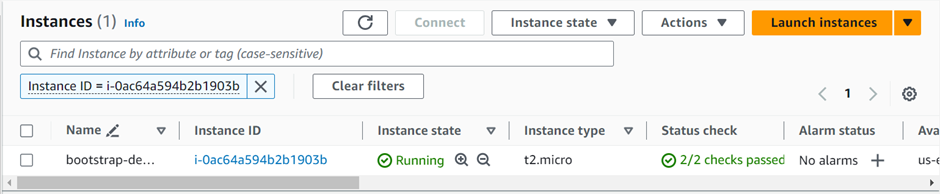
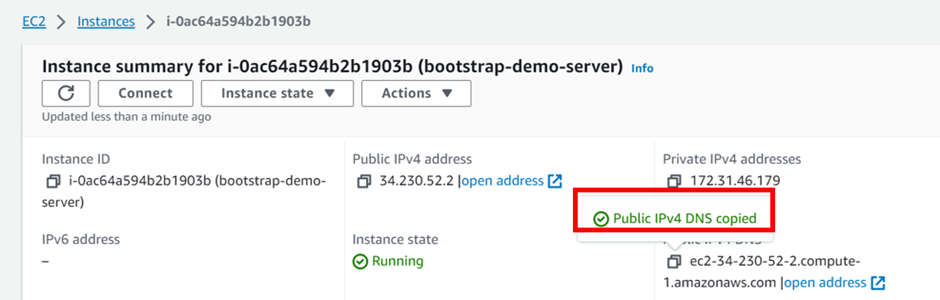
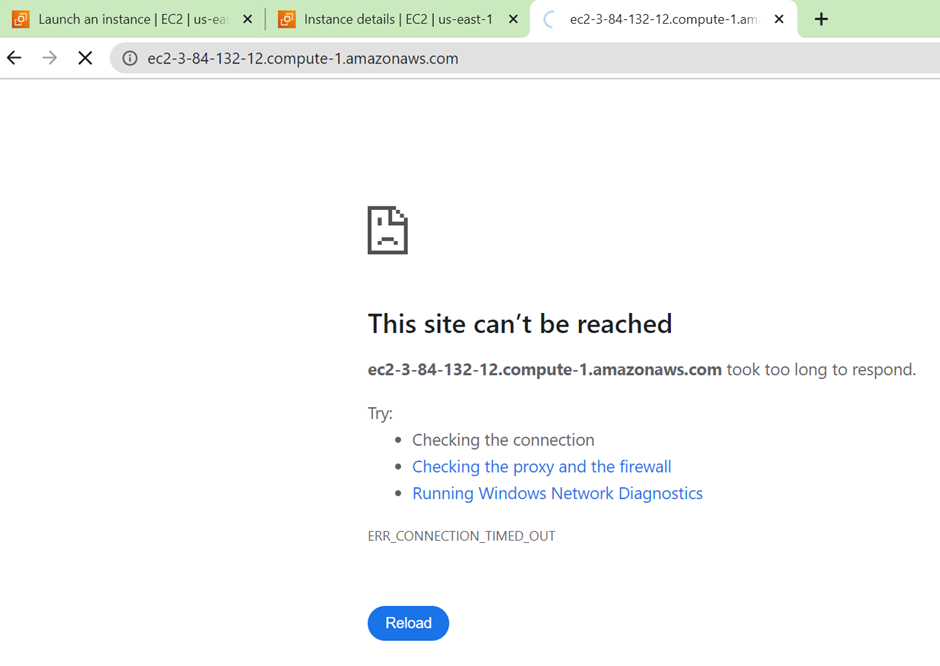
We are getting this error because HTTP port 80 is not open, we will go back to our instance modify security group, and open port 80.
Select your instance and click the instance state dropdown move to security then click modify security group.
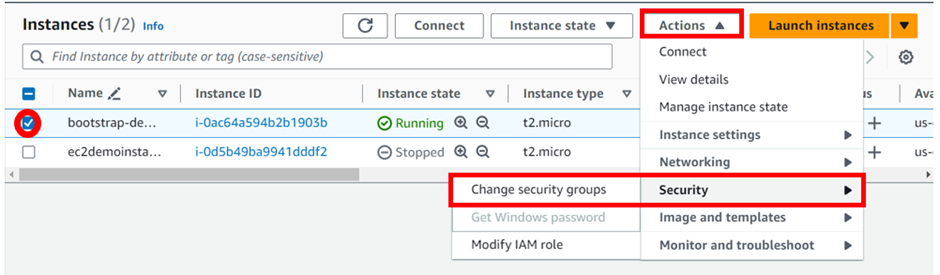
Under the associated security group, select the search box and look for the web traffic security group which opens port 80 and 443 select it, then click save.
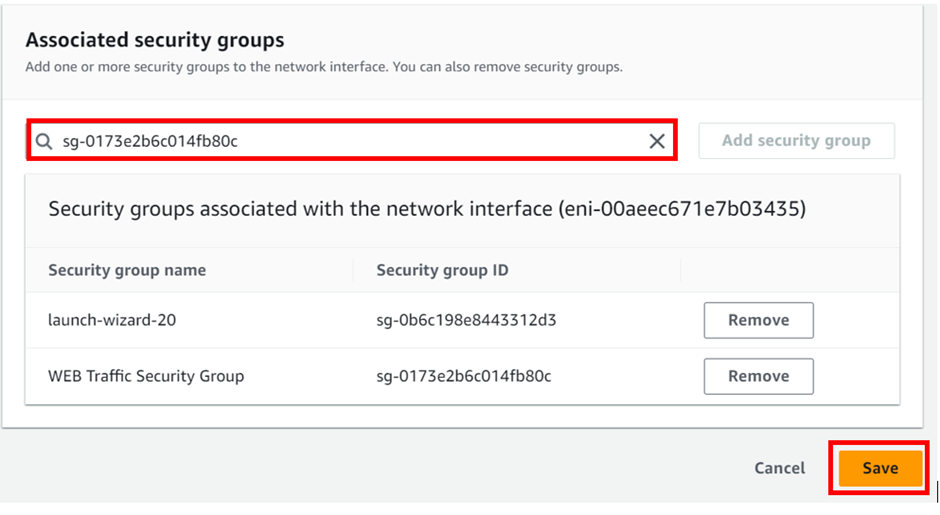
Now come back to your instance copy its public DNS and paste it into your browser.
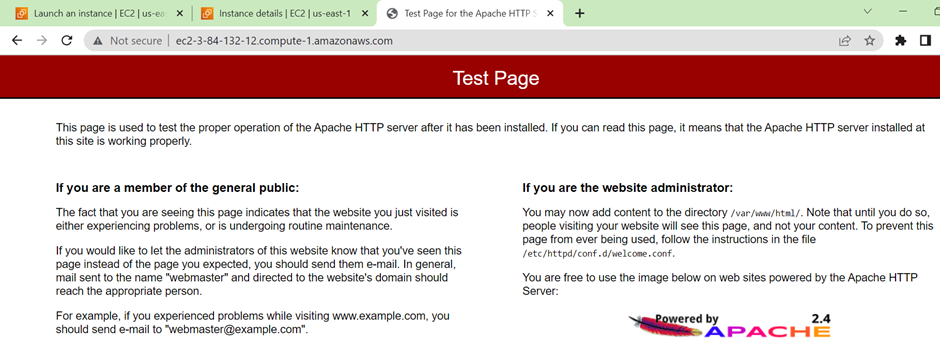
Congratulations, we can now access our HTTP web traffic on port 80. This clearly shows how security groups can allow or deny internet traffic.
Again, remember this instance was bootstrapped and installed Apache on launch.
Pull everything down and stay tuned for more.
If you have any questions concerning this article or have an AWS project that requires our assistance, please reach out to us by leaving a comment below or email us at. [email protected]
Thank you!
